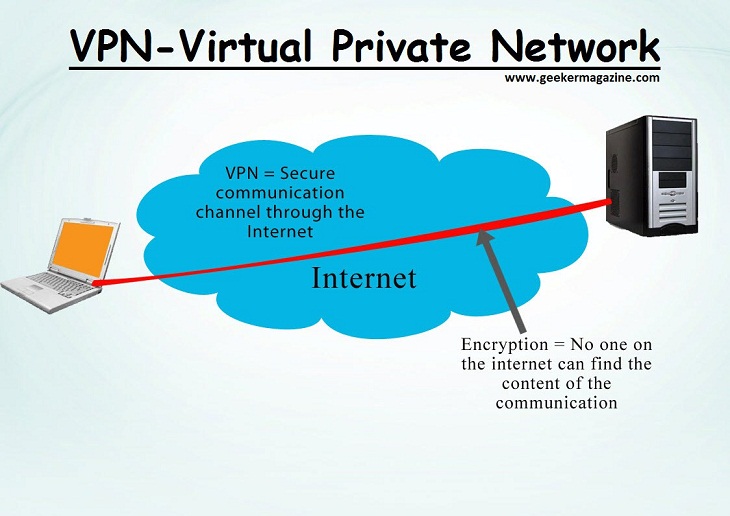
Virtual Private Network (VPN), allows users to set up a network virtual private network with another network on the Internet. Let’s learn more about VPN virtual private network, commonly used protocols and advantages and disadvantages please!
I. What is a VPN virtual private network?
1. What is VPN?
- VPN, also known as Virtual Private Network, allows users to set up a virtual private network with another network on the Internet.
- VPN can be used to access geo-restricted websites, protect your browsing from “prying” on public Wi-Fi by setting up a virtual private network for you.
- If you want to connect to the VPN system, each account must be authenticated (Username and Password are required).
- These account credentials are used to grant permissions. Access through 1 data – Personal Identification Number (PIN), these PIN codes are usually only valid for a certain period of time (30 seconds or 1 minute).
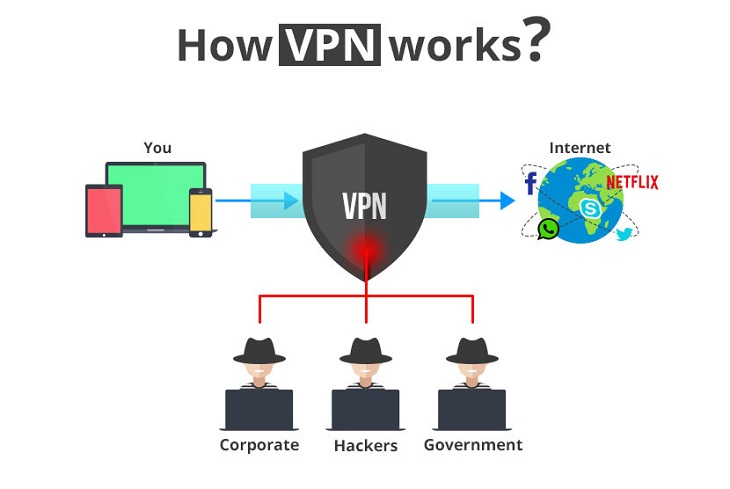
- In the past, VPNs were mainly used by businesses that wanted to connect many geographically distant branches, or create an environment that allowed employees to connect to the office network to working remotely while still ensuring security.
- Nowadays, VPN is gradually becoming an important and popular service for most individual users, in order to protect them from attack when connecting to a public network.
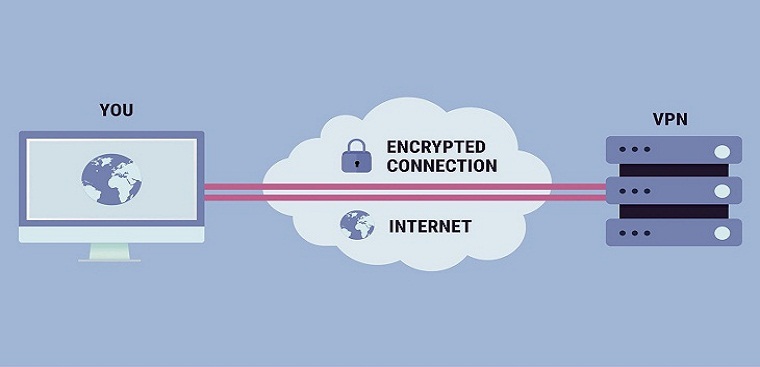
- When browsing the web with a VPN, laptop will contact the website through an encrypted VPN connection. All requests, information and data exchanged between you and the website will be transmitted in a secure connection. If you use a VPN in the US to access Netflix, Netflix will see your connection coming from the US.
2. VPNs are used to do a lot of things like:
- Access to business network while away: VPN is commonly used by business people to access their business network, including all resources. on the local network, while on the road, traveling,… Intranet resources do not need to be in direct contact with the Internet, thereby increasing security.
- Access your home network, even when you’re not at home: You can set up your own VPN to access when you’re not at home. This will allow remote access to Windows via the Internet, use files shared in the local network, play computer games over the Internet as if you were on the same LAN.
- Browse anonymously: If you are using public WiFi, browsing the web on non-https sites, the safety of data exchanged in the network will be exposed. If you want to hide your browsing activity to make your data more secure, you should connect to a VPN. All information transmitted over the network will now be encrypted.
- Access geo-restricted websites, bypass Internet censorship, bypass firewalls,…
II. Protocols commonly used in VPN
1. IP security (IPSec)
Used to secure communications, data flows in the Internet environment (environment outside the VPN). This is the bottom line, traffic over IPSec is used mainly by Transport modes, or tunnels (or tunnels – this concept is often used in Proxy, SOCKS) to ENcrypt data in VPN.
The difference between these modes is:
- Transport mode is only responsible for encrypting data inside packages (data packages – or also known as payloads). While tunnels encrypt all those data packages.
- Therefore, IPSec is often referred to as Security Overlay, because IPSec uses layers of security compared to other protocols.
2. Secure Sockets Layer (SSL) and Transport Layer Security (TLS)
There is a similar part to IPSec, the two protocols above also use passwords to ensure safety between connections in the Internet environment.
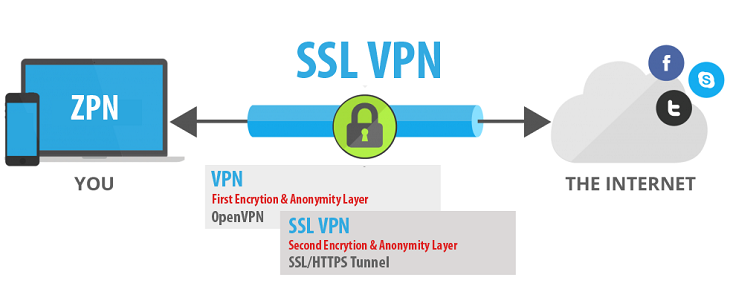
- Besides, the above two protocols also use Handshake mode – related to the account authentication process between client and server. For a connection to be considered successful, this authentication process will use Certificates – which are account authentication keys stored on both the server and the client.
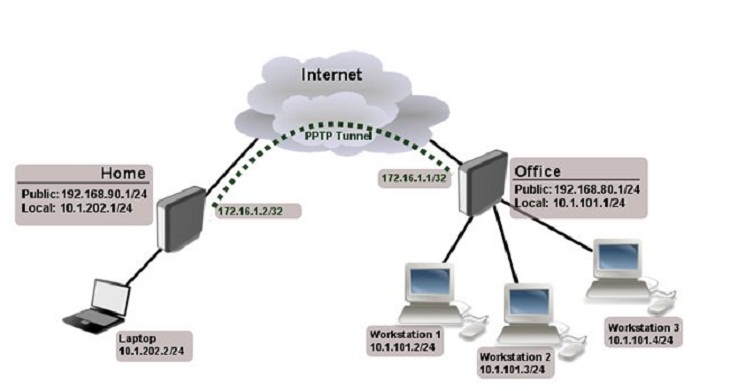
3. Point-To-Point Tunneling Protocol (PPTP):
- A protocol used to transmit data through tunnels – Tunnels between two traffic layers in the Internet. L2TP is also often used in tandem with IPSec (acting as Security Layer – mentioned above) to ensure smooth transmission of L2TP data over the Internet environment.
- Unlike PPTP, VPN will “inherit” the entire L2TP/IPSec layer that has shared account authentication keys or Certificates.
III. Advantages and disadvantages of VPN
1. Advantages
- To build a private network, a virtual private network, using a VPN is an inexpensive solution. Compare the convenience that VPN brings with the cost to you. set up a system as you like, obviously VPN prevails.
2. Cons
- VPN does not have the ability to manage Quality of Service (QoS) over the Internet environment, so data packets – Data packages are still at risk of being lost, risky.
- The management ability of VPN providers is limited, so your computer can still be hacked, potentially posing a security risk to your computer.
References: https://dienmayxanh.com/
Thanks for watching!!!











 Tiếng Việt
Tiếng Việt